Contact Information
Tech Digital Minds
Top Stories
ALL TOP STORIES
Incident Response & Recovery: A Complete Guide to
- . 21 February 2026
- 4 Views
-
Shares

Looking Toward 2026: The Future of Cybersecurity in Health-ISAC
- By James
- 161 Views
Six Ways to Prepare for a More Secure Future In today’s rapidly evolving digital landscape, preparing for a secure future has never been more crucial.

DPDPA and Media Data Privacy
- By James
- 99 Views
Understanding the Digital Personal Data Protection Act (DPDPA) 2023 The landscape of data privacy in India is undergoing a significant transformation with the introduction of

ESET Small Business Security Review: An In-Depth Look at a Robust Security Solution for Expanding Enterprises
- By James
- 39 Views
ESET NOD32 Antivirus: A Comprehensive Review When it comes to safeguarding your digital world, choosing the right antivirus software is paramount. Among the myriad options,

Mandiant’s AuraInspector Safeguards Against Salesforce Issues
- By James
- 56 Views
Mandiant’s AuraInspector: Safeguarding Salesforce Experience Cloud Mandiant has stepped up its commitment to enhancing cybersecurity with the release of AuraInspector, a powerful open-source tool explicitly

ESET Home Security Essentials Review: Comprehensive Features and Outstanding Lab Performance
- By James
- 53 Views
ESET provides a commendable range of free Android antivirus protection, although this offer comes with notable limitations. Users eager to take advantage of the full

Legal Assessments of Warfare Algorithms: From Cyber Weapons to AI Technologies
- By James
- 123 Views
The Legal Review of AI-Enabled Weapons: Insights from Cyber Weapon Regulations Introduction to Legal Reviews in Warfare As warfare evolves, so too must the legal

Deepfake Blackmail: How to Protect Yourself in 2025
- By James
- 487 Views
Introduction The rapid advancement of artificial intelligence has given rise to deepfake technology, making it easier than ever for scammers to create highly realistic fake

2025 Recap: Enhancing Cybersecurity in EMEA through AI Innovations
- By James
- 117 Views
Cybersecurity Resilience in EMEA: A Transformative Journey in 2025 As 2025 begins to draw to a close, the landscape of cybersecurity across Europe, the Middle
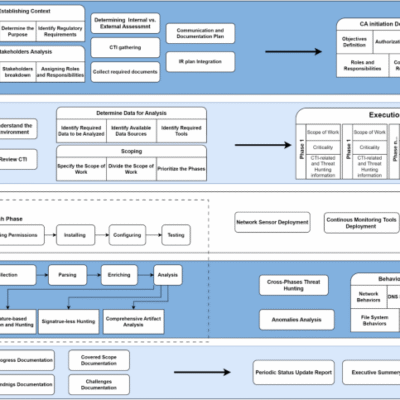
Proactive Detection of Cybersecurity Breaches Using the PROID Compromise Assessment Framework
- By James
- 233 Views
Unveiling the PROID CA Framework: A Standardized Approach to Compromise Assessment As the digital landscape continues to evolve, so do the complexities of IT environments.

Understanding Machine Learning: A Beginner-to-Pro Guide
- By James
- . 23 September 2025
- 824 Views
-
Shares

The Truth About Rug Pulls: How to Spot and Avoid Crypto Exit Scams
- By James
- . 29 July 2025
- 805 Views
-
Shares

5 Common Crypto Scams and How to Avoid Them
- By James
- . 29 July 2025
- 863 Views
-
Shares

Safeguarding Your Digital Fortress: Why Cybersecurity is Your Business’s Lifeline
- By James
- . 10 August 2024
- 1,316 Views
-
Shares
Recent News
ALL RECENT NEWS
How to Leverage AI for Business Automation: A Step-by-Step Guide
- By James
- . 24 May 2025
- 921 Views
-
Shares

Natural Disasters: The Unpredictable Threats to Security
- By James
- . 4 September 2024
- 1,229 Views
-
Shares

Quantum Computing Breakthrough: What It Means for Your Smartphone’s Future
- By James
- . 3 August 2024
- 1,281 Views
-
Shares

AI Revolution: How Artificial Intelligence Will Transform and Change the World
- By James
- . 12 July 2024
- 1,463 Views
-
Shares





