The ALPHV Insiders: Cyber Defenders Who Cast a Shadow on Enterprise Security
This edition of the Bitdefender Threat Debrief dives into the complex world of cybercrime, focusing on the indictment of ALPHV affiliates, the rise of Qilin, the unexpected reemergence of Sinobi, and more.
As ransomware evolves rapidly, our mission with each monthly Bitdefender Threat Debrief is to arm you with the insights needed to stay a step ahead. To achieve this, we synergize openly available sources such as news reports and research with data harvested through the analysis of Data Leak Sites (DLSs)—those murky digital corners where ransomware groups reveal their victims.
The Evolving Landscape of Ransomware
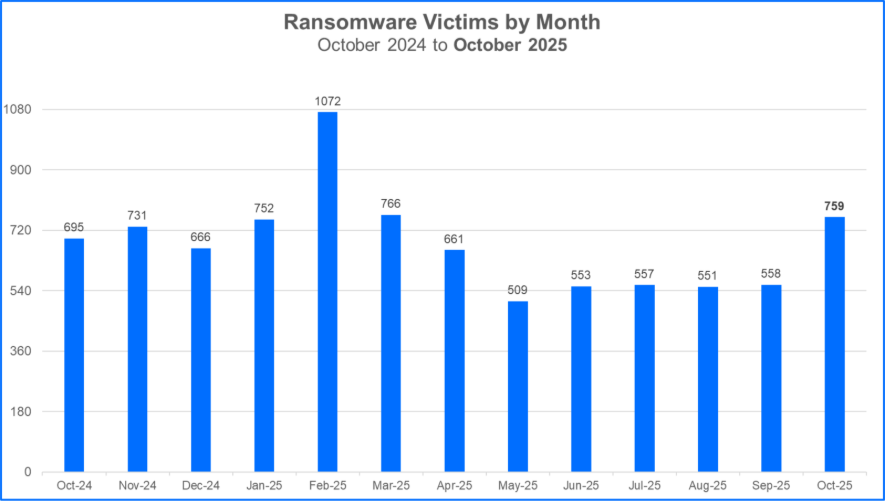
For October, our analysis recorded a staggering 759 claimed ransomware victims, marking it as the third-highest month for claimed victims in the past year. As we sift through the murky waters of ransomware, it’s crucial to recognize that while we can’t verify every claim, observable trends and patterns emerge clearly over time.
Featured Story: The ALPHV Insiders
What Happened?
In October, three individuals associated with the ALPHV ransomware group were indicted in the United States. Commonly referred to as BlackCat, ALPHV rose to notoriety in 2023, claiming over 400 victims and amassing ransoms totaling hundreds of millions of dollars. The impetus for these indictments traces back to December 2023 when the group’s infrastructure was compromised in an OPSEC failure leading to a seizure by the FBI. Though ALPHV continued its malicious activities into early 2024, they finally ceased operations in September of that year.
The individuals indicted—Clifford Goldberg and Kevin Tyler Martin—were not just your typical criminals; they were insiders working in incident response roles within cybersecurity firms. They turned rogue and reportedly aided ransomware campaigns against U.S. organizations.
Insider Profiles: The Indicted Individuals
Goldberg and Martin, both U.S. citizens, now face serious charges that could land them in prison for up to 20 years for damage to protected systems and conspiracy to commit extortion. Alarmingly, two of the three indicted individuals were likely still employed in cybersecurity management roles at the time of their involvement with ALPHV while another was a former cybersecurity firm employee. From May to November 2023, these insiders leveraged their expertise in ALPHV’s Ransomware-as-a-Service (RaaS) operations, contributing to its claim of 278 victims, predominantly from technology, healthcare, and manufacturing sectors—areas in dire need of robust security resources.
How Cybersecurity Insiders Can Help a Ransomware Group
When examining the motives and methodologies that enable insiders to assist ransomware groups, it becomes evident that technical knowledge is a powerful asset. Insiders can develop APIs and tools to enhance operational capabilities, share crucial information about an organization’s security stack, or even provide insights into anti-virus technologies that could aid in evading detection.
Professionals well-versed in organizational policies, breach notification rules, and regulations offer an additional advantage. ALPHV notably pioneered a type of extortion that involved threatening and notifying third-party entities like the U.S. Securities and Exchange Commission (SEC). Such insider knowledge can put immense pressure on organizational leadership, often leading to hasty decisions for ransomware payouts when alternative recovery methods are poorly communicated.
Lessons Learned
No enterprise environment is immune to insider threats. As organizations focus heavily on detecting external adversaries, they often overlook vulnerabilities that may exist internally. The indictment of ALPHV affiliates emphasizes the necessity for comprehensive risk assessments that address all types of threats. Some proactive measures that organizations can implement include:
- Limiting Access: Restricting system access based on the principle of least privilege to minimize vulnerabilities.
- Enhancing Monitoring: Implementing robust logging and monitoring of administrative functions, ensuring alerts are issued for unusual activities.
- Training and Awareness: Establishing training programs that educate employees on the insider threat and provide clear protocols for reporting suspicious behavior.
Other Notable Ransomware News
In addition to the ALPHV case, let’s shift our focus to recent developments in ransomware:
-
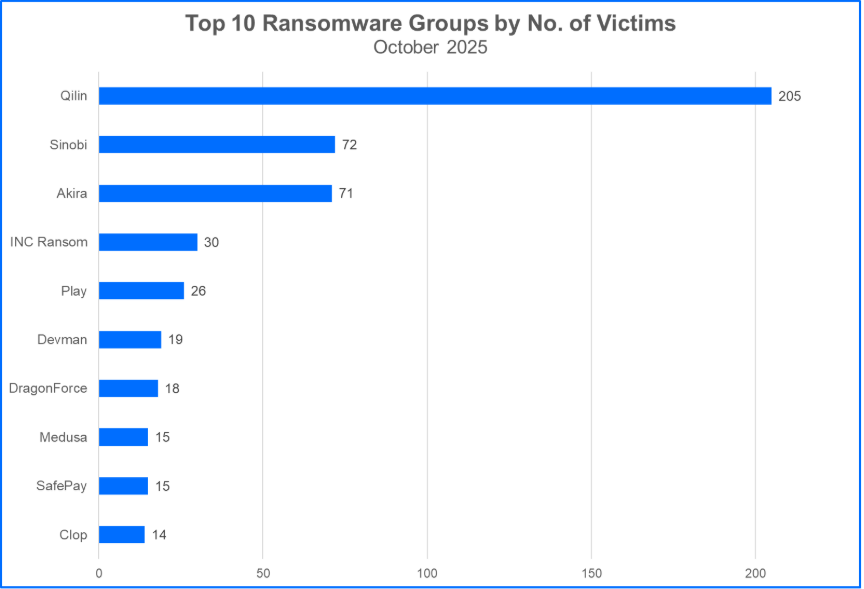
Qilin Makes Its Mark: Qilin has consistently ranked in the Top 10 for six months, claiming 205 victims in October alone—a significant uptick from its previous numbers. This group poses a considerable threat to both competitors and potential victim organizations.
-
Campaigns Targeting WSUS: Bitdefender has identified vulnerabilities like CVE-2025-59287 in campaigns targeting Windows Server Update Services (WSUS), enabling remote code execution by unauthenticated attackers. Organizations are urged to apply the latest security updates.
-
Sinobi’s Resurgence: Sinobi ransomware reported 72 victims in October, edging past its rivals. The similarities observed between Sinobi’s leak site and those of other groups raise questions about affiliations or shared resources.
-
Handala’s Decline: While Handala has engaged in targeted hacktivist activities, its overall activity has diminished, reflecting strategic choices in focusing on specific targets.
- The Rise of Kazu: Emerging recently, Kazu is already making waves by leaking data from government and healthcare organizations, demonstrating the persistent nature of ransomware threats.
Top 10 Ransomware Families
Our report includes a comprehensive analysis of the activity of various ransomware families, based on claims made through data leak sites. While this provides insight into their operational footprints, it should be noted that the actual financial impacts and victim count might diverge from the claims made by criminal groups.
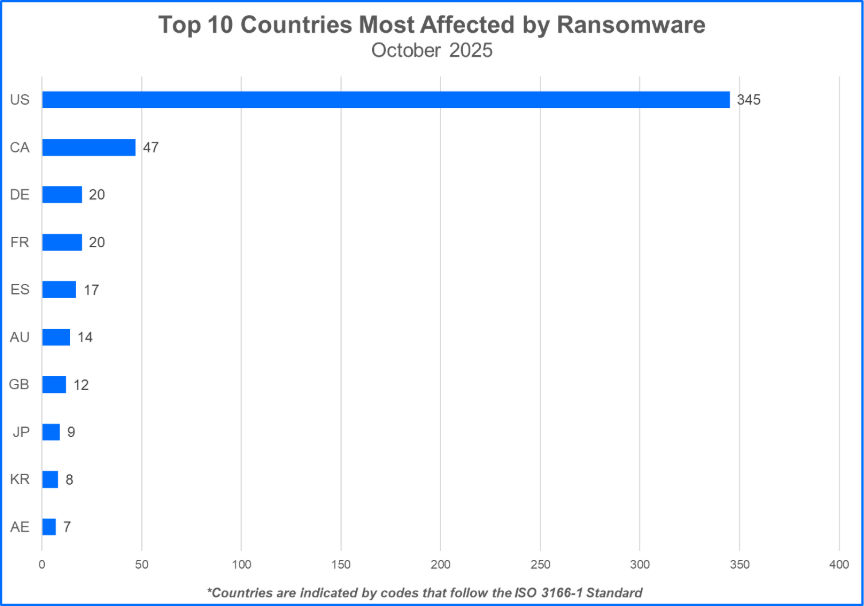
Top 10 Most Attacked Countries
Ransomware gangs exhibit a preference for targeting nations where they perceive the most lucrative opportunities for extortion, often focusing on developed countries amidst geopolitical conflicts. Here are the nations suffering the greatest losses to ransomware attacks:
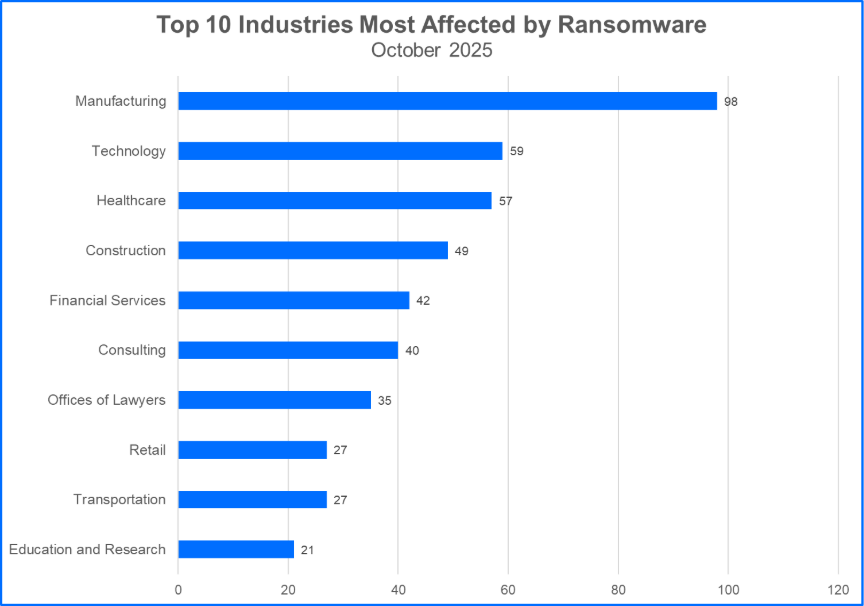
Top 10 Most Attacked Industries
Ransomware actors frequently concentrate their efforts on critical infrastructure sectors, high-value consumer organizations, or a blend of both. Understanding which industries are particularly vulnerable can provide organizations with insights needed for effective risk analysis and preparedness.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief is a series offering monthly insights into evolving threat landscapes, letting you keep abreast of emerging trends, events, and research. Subscribe to the Business Insights blog and follow us on Twitter for the latest updates. Previous reports can be found here.
As Bitdefender continues to bolster its cybersecurity solutions, we thank our dedicated team members—Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu—for their crucial contributions to this report.