Protecting Sensitive Data: Best Practices for Physical Security Teams
In an era where data breaches and cyber threats are increasingly prevalent, the responsibility of safeguarding sensitive data falls not just on IT teams but also heavily on physical security departments. As we observe Data Protection Day, Genetec Inc. shares essential recommendations aimed at helping organizations protect sensitive physical security data while ensuring effective security operations.
The Significance of Physical Security Data
Physical security systems generate vast amounts of information daily—ranging from video footage and access control logs to license plate recognition data. This information has become crucial for operational efficiency and investigative processes. However, the rise of privacy regulations and heightened public expectations around data transparency compel organizations to manage this information responsibly.
The Challenge of Sensitive Data
Mathieu Chevalier, Principal Security Architect at Genetec Inc., emphasizes that physical security data is inherently sensitive. It requires more than basic protective measures. "Organizations should expect clear limits on how their data is used and maintained," he notes. It’s vital to protect this information not just from unauthorized access but also from being exploited beyond its intended use.
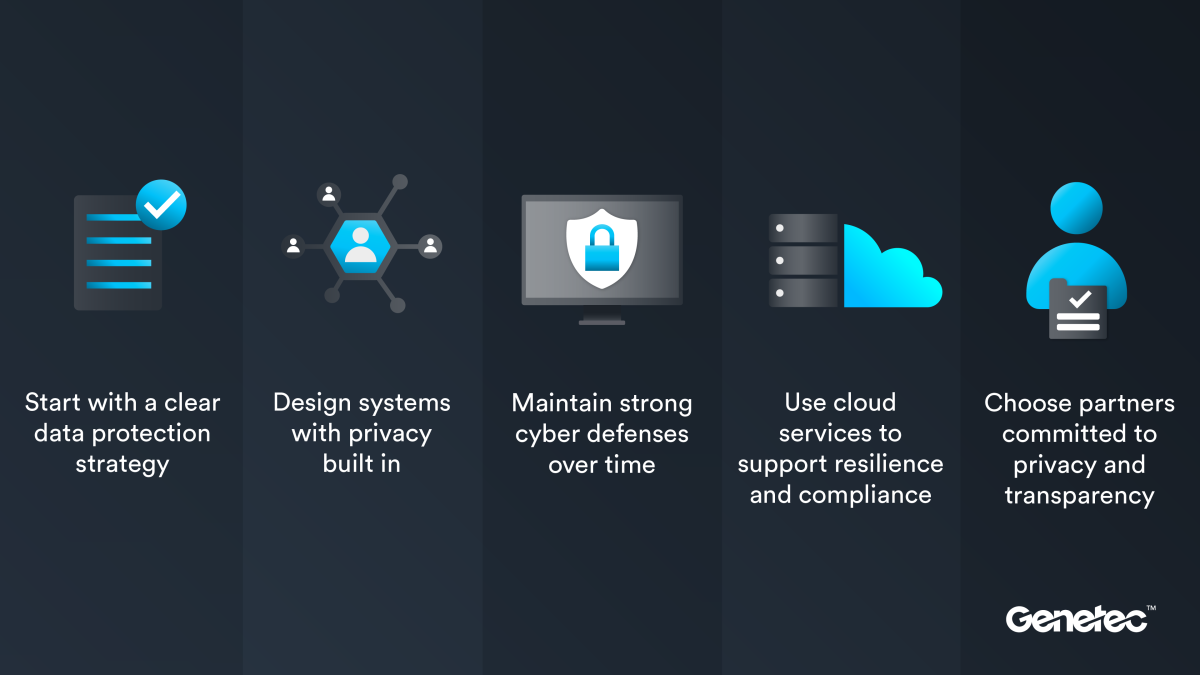
Establish a Clear Data Protection Strategy
An effective first step for organizations is to assess what data they collect. This involves understanding:
- Purpose: Why is the data being collected?
- Storage: Where is it being stored?
- Retention: How long will it be retained?
- Access: Who can access this data?
Documenting these practices is essential. Not only does this minimize unnecessary data exposure, but it also helps identify policy gaps that may affect compliance as regulations continue to evolve. Transparency in data handling practices builds trust with employees, customers, and the public.
Design Systems with Privacy in Mind
The principle known as privacy-by-design serves as a cornerstone for managing sensitive data. This concept goes beyond implementing security controls; it encompasses how personal data is collected, utilized, and governed throughout its lifecycle.
Leveraging data minimization strategies ensures that only essential data—pertinent to specific security objectives—is collected. Implementing strong security measures like data encryption, strong authentication, and granular access controls significantly reduce the risk of unauthorized access. Furthermore, employing privacy-enhancing technologies—such as anonymization and data masking—can safeguard individual identities while maintaining the operational value of security data.
Maintain Strong Cyber Defenses
Data protection is not a one-time effort; it’s ongoing. Establish a robust framework for regular system hardening, vulnerability management, and timely software updates to mitigate new cybersecurity threats as they arise. Treating privacy and cybersecurity as continuous operational responsibilities fortifies the organization’s overall security posture.
Embrace Cloud Services for Compliance
Organizations are increasingly leveraging cloud-managed solutions and software-as-a-service deployments. These tools not only ensure that security patches and privacy controls are updated regularly but also reduce the burden on internal teams. By adopting flexible deployment strategies, organizations can better balance scalability, control, and compliance with data residency prerequisites across on-premises and cloud environments.
Choose Partners Committed to Privacy
Selecting the right technology partners is vital. Organizations should evaluate potential vendors based on their governance of personal data, clear definitions of data use, and transparent communication regarding privacy practices. Independent security standards, such as ISO/IEC 27001 and SOC 2 Type II reports, can provide necessary assurances about the protection and management of systems and data.
When assessing vendors, consider their:
- Vulnerability disclosure processes
- Data governance practices
- Approach to artificial intelligence, particularly regarding transparency and human oversight
Continuous Improvement and Education
As privacy regulations and industry standards evolve, organizations must remain proactive. Continuous education and training for teams on the latest data protection strategies and regulatory requirements ensure that everyone is up-to-date with best practices. Regular assessments and updates to data protection strategies help organizations stay ahead of potential risks and vulnerabilities.
For those looking to deepen their understanding of data protection strategies specific to physical security systems, Genetec’s comprehensive resources serve as an invaluable tool.
By implementing these best practices, organizations can effectively navigate the complex landscape of data protection while ensuring the safety of sensitive information in their physical security operations.