Contact Information
Tech Digital Minds
Top Stories
ALL TOP STORIES
Incident Response & Recovery: A Complete Guide to
- . 21 February 2026
- 1 Views
-
Shares
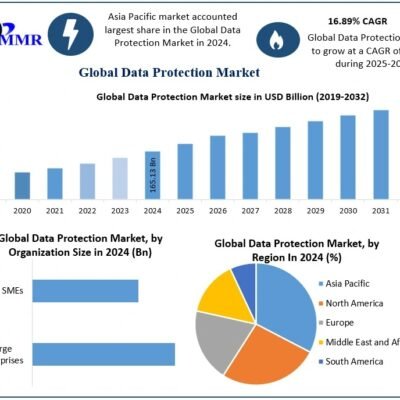
Data Protection Market Expected to Surpass USD 575.50 Billion by 2032 Amid Growing Cybersecurity Threats
- By James
- 214 Views
Understanding the Data Protection Market: Insights and Trends As businesses increasingly navigate a digital landscape replete with data challenges, understanding the data protection market becomes

Top 10 Threat Actor Trends for 2025 and What to Watch for in 2026
- By James
- 78 Views
The Evolution of Cybercrime: Understanding Today’s Threat Actors The landscape of cybercrime has dramatically transformed from its early days. In the 1990s, hackers often operated

Weekly Update: PoC for Trend Micro Apex Central RCE Released and Patch Tuesday Preview
- By James
- 55 Views
Cybersecurity Week in Review: Key Developments In the ever-evolving landscape of cybersecurity, staying informed is crucial. Last week’s news cycle brought to light several compelling

Top 6 Identity Theft Protection Services for January 2026
- By James
- 77 Views
Understanding the Importance of Identity Theft Protection Identity theft has transformed into a complex and daunting issue, far more sophisticated than merely lost wallets or

Affordable Security Tools for Startups and Freelancers: Cybersecurity for SMBs in 2025
- By James
- 360 Views
Introduction: Why Cybersecurity Can’t Be Ignored by Small Businesses Cybersecurity is no longer just a concern for Fortune 500 companies. In fact, cybercriminals increasingly target

Top Employee Monitoring Software Reviews for 2025
- By James
- 607 Views
The Best Employee Monitoring Software for Small Businesses: A Comprehensive Guide In the fast-paced world of small business management, effective employee monitoring software can be

Top 10 Leading End-to-End Threat Intelligence Companies of 2025
- By James
- 312 Views
The Rising Importance of End-to-End Threat Intelligence in 2025 In 2025, businesses are grappling with an increasingly perilous digital landscape. Cyberattacks have evolved in sophistication,

Deepfake Blackmail: How to Protect Yourself in 2025
- By James
- 485 Views
Introduction The rapid advancement of artificial intelligence has given rise to deepfake technology, making it easier than ever for scammers to create highly realistic fake

3 Emerging Phishing Threats: Clone, Deepfake, and CAPTCHA Challenges
- By James
- 38 Views
Deepfake Phishing What is Deepfake Phishing? Deepfake phishing is an innovative and alarming tactic that leverages artificial intelligence (AI) to create realistic audio or video

Understanding Machine Learning: A Beginner-to-Pro Guide
- By James
- . 23 September 2025
- 822 Views
-
Shares

The Truth About Rug Pulls: How to Spot and Avoid Crypto Exit Scams
- By James
- . 29 July 2025
- 803 Views
-
Shares

5 Common Crypto Scams and How to Avoid Them
- By James
- . 29 July 2025
- 859 Views
-
Shares

Safeguarding Your Digital Fortress: Why Cybersecurity is Your Business’s Lifeline
- By James
- . 10 August 2024
- 1,314 Views
-
Shares
Recent News
ALL RECENT NEWS
How to Leverage AI for Business Automation: A Step-by-Step Guide
- By James
- . 24 May 2025
- 919 Views
-
Shares

Natural Disasters: The Unpredictable Threats to Security
- By James
- . 4 September 2024
- 1,227 Views
-
Shares

Quantum Computing Breakthrough: What It Means for Your Smartphone’s Future
- By James
- . 3 August 2024
- 1,279 Views
-
Shares

AI Revolution: How Artificial Intelligence Will Transform and Change the World
- By James
- . 12 July 2024
- 1,461 Views
-
Shares





