Contact Information
Threat Intelligence
Stay ahead of cybercriminals with deep dives into emerging threats, malware trends, and evolving attack techniques. Understand the threat landscape to better protect your data, systems, and digital assets.

Germany’s Evolving Cyber Threat Landscape and Risks for SMEs
- By James
- . 16 November 2025
Germany’s Growing Threat Landscape: An Urgent Call to Action for IT Security Germany’s digital environment has reached a critical juncture. The Federal Office for Information

Bitdefender Threat Report | November 2025
- By James
- . 15 November 2025
The ALPHV Insiders: Cyber Defenders Who Cast a Shadow on Enterprise Security This edition of the Bitdefender Threat Debrief dives into the complex world of
Disrupting the First Documented AI-Driven Cyber Espionage Campaign | Anthropic
- By James
- . 14 November 2025
The Intersection of AI and Cybersecurity: A New Era of Threats In recent discussions regarding cybersecurity, a pivotal point has emerged: the rise of artificial

HSCC Unveils 2026 AI Cybersecurity Guidelines: Key Best Practices for Healthcare Organizations
- By James
- . 13 November 2025
Navigating the Future of AI Cybersecurity in Healthcare: Insights from the HSCC The Health Sector Coordinating Council (HSCC), through its dedicated Cybersecurity Working Group (CWG),

Companies Seek Enhanced Value from Their Threat Intelligence Platforms
- By James
- . 12 November 2025
Understanding the Challenges of Threat Intelligence Platforms Dive Brief The landscape of threat intelligence is continually evolving, with businesses now more reliant than ever on

Current Cybersecurity Job Openings: November 11, 2025
- By James
- . 11 November 2025
The Growing Demand for Cybersecurity Professionals: A Snapshot of Current Job Openings In an era dominated by digital transformation, cybersecurity has emerged as a cornerstone

CISA’s Expiration Creates a Risky Gap in U.S. Cyber Collaboration
- By James
- . 10 November 2025
The Expiration of the Cybersecurity Information Sharing Act: A Sea Change in Cyber Defense On September 30, 2025, the Cybersecurity Information Sharing Act (CISA 2015)

The Potential Effects of a Government Shutdown on Hospital Cybersecurity – Health-ISAC
- By James
- . 9 November 2025
Heightened Cybersecurity Risks Amid Government Shutdown: A Looming Threat for Hospitals As the government shutdown persists, a growing concern emerges within the healthcare sector: an

The Role of a SOC Manager: Key Responsibilities and Career Advancement Opportunities
- By James
- . 8 November 2025
What is a SOC Manager? A Security Operations Center (SOC) manager plays a crucial role in cyber defense, leading a team responsible for continuously monitoring,
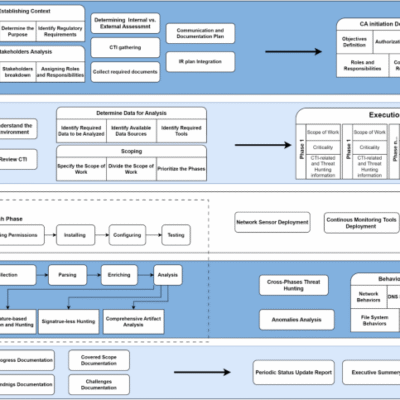
Proactive Detection of Cybersecurity Breaches Using the PROID Compromise Assessment Framework
- By James
- . 7 November 2025
Unveiling the PROID CA Framework: A Standardized Approach to Compromise Assessment As the digital landscape continues to evolve, so do the complexities of IT environments.
